Unsure which services you need?
Take our short quiz and get expert recommendations to transform your business with the right technology solutions.
With InterVision® as your technology partner, you can focus on what you do best, while we take care of the rest
We empower businesses to thrive with industry-leading technology solutions by leveraging our award-winning services.
Our team of experts brings unmatched knowledge and experience, providing proactive monitoring, maintenance, and support to keep your business running securely and smoothly 24/7.
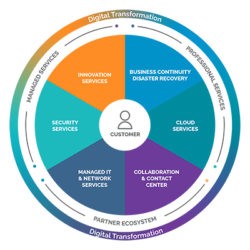
The right fit is in our DNA
Our expansive technology service offerings, broad partner ecosystem, and consultative approach mean that we think together and engage deeper to find the “perfect fit” solution for you.
Future-ready customers
Empowering forward-thinking customers to collaborate, innovate boldly, and engage deeply to create exceptional experiences.











Featured resources
Explore our featured resources to help you stay informed and empowered to achieve your goals.
Awards
We’ve received numerous awards and recognition for our innovative solutions, exceptional service, and commitment to customer success.
































